#PrivacyByDefault #MassEncryption
There are two kinds of users: The ones, who encrypt their stuff and the ones, who never had lost something or never got something stolen.
Imagine your Laptop being stolen on the train. Not only, you probably lost all of your data (Backups!), but also there is now a stranger that has access to potentially very private data - Pictures of your last birthday, company records you need to keep secret or the new piece of code that is awesome and the capital of your startup you just wanted to create.
Plenty of reasons for investing a little bit of time in your digital self-defence, and a sane full-disk encryption is a major part of it.
I personally have two different approaches: VeraCrypt (successor of TrueCrypt after they surprisingly closed, leaving lots of speculations about their non-commitment to build in a secret backdoor for a large state agency, but that is based on pure speculation and is on the list of conspiracy theorems that probably turn out to be at least somehow concise enough to be taken seriously.) or LUKS.
This article covers LUKS, because I consider this the canonical way for every mature Linux environment.
Recipe
Assuming the HDD is /dev/sdb and you want to call it Cryptodisk
- Reformat the external HDD. Create a single partition with any filesystem (we will overwrite this in the next step)
- Make sure all filesystems for that disk are unmounted.
cryptsetup -y -v luksFormat /dev/sdb1- Enter passphrase.
- Write the passphrase on a sheet of paper and store it on a safe place.
- REALLY do it. You probably will forget the passphrase and then you can cry your data goodbye
- Open the crypdevice:
cryptsetup luksOpen /dev/sdb1 Cryptodisk mkfs.xfs /dev/mapper/Cryptodiskcryptsetup luksClose Cryptodisk- Plug the disk out and re-plug it in. In your file explorer (tested with caja) it should appear as encrypted device.
If you click on it, it asks for the passphrase and it will be mounted.
Alternatively, use
cryptsetup luksOpen /dev/sdb1 Cryptodisk && mount /dev/mapper/Cryptodisk /mnt/Cryptodisk
Note: It’s possible to compartmentalize multiple partitions by putting a LVM volume atop cryptsetup. This is more advanced but pretty much straightforward. The Arch Wiki is your friend.
Step by Step guide
I plug in my HDD and assume it’s gonna be recognised as /dev/sdb.
First, We need to make sure that it’s unmounted
$ sudo umount /dev/sdb?
Next, format the HDD. I normally use parted, users who prefer a GUI can user gparted as well. So, let’s use start gparted on the disk
$ sudo gparted /dev/sdb
# In Wayland this might cause trouble, as sudo and wayland are not super nice to each other ... That's beyond the scope of what I write down here, sorry :-)
Now: MAKE SURE IT’s THE RIGHT DISK.. Are you sure? Double-check it. Do the partitions look like the ones expected? Is there anything fishy? Once you clear your partition table or (even worse) wrote a new filesystem, it’s unlikely you can fetch your data without any losses. Take a breath and triple-check before doing anything.
OK. Then create the partition. Select a random filesystem (or raw or unformatted), as we are anyways going to create our own afterwards. It’s only important to create the layout correctly. In my case it looks like the following: one partition that takes the full space (Little bit of empty space at the end is needed by GPT for the Backup table)
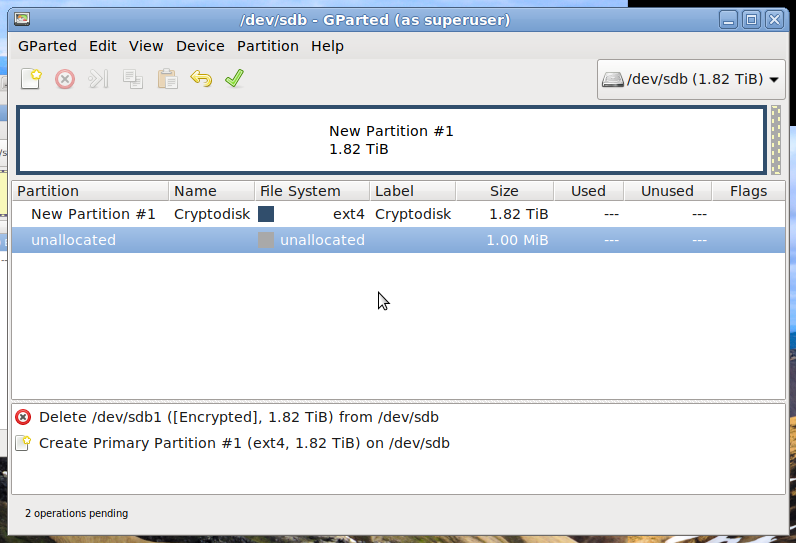
Close gparted and encrypt the partition using cryptsetup:
$ sudo cryptsetup -y -v luksFormat /dev/sdb1
WARNING!
========
This will overwrite data on /dev/sdb1 irrevocably.
Are you sure? (Type uppercase yes): YES
Enter LUKS passphrase:
Verify passphrase:
Command successful.
Congratulations, you created your first encrypted partition! Now we are gonna put a filesystem on that one, so you can actually use it :-)
So, we are gonna “open” the cryptdevice. This means, we are making the crypto layer, atop which we can run our filesystem
# Assuming you want to name it Cryptodisk. The name doesn't matter, it's just for the system to find the device
$ sudo cryptsetup luksOpen /dev/sdb1 Cryptodisk
cryptsetup asks for the Passphrase. After successfully opening the device, it will be listed as /dev/mapper/Cryptodisk
Now we create a filesystem. I chose xfs because it’s a stable working horse, that runs everywhere, but you can choose whatever you want.
$ sudo mkfs.xfs /dev/mapper/Cryptodisk
Great, now you’ve created the filesystem. Close the disk with cryptsetup
$ sudo cryptsetup luksClose Cryptodisk
$ sync
Wait until everything on the disk has been written (it stops flashing, depending on your disk) and unplug the disk.
The next time you plug your disk in, it will be recognised by caja/nemo as Encrypted Device, you type in your Passphrase and it will be automatically mounted (or with cryptstetup luksOpen and mount but the purpose was to create a convenient way to work with your external disks).
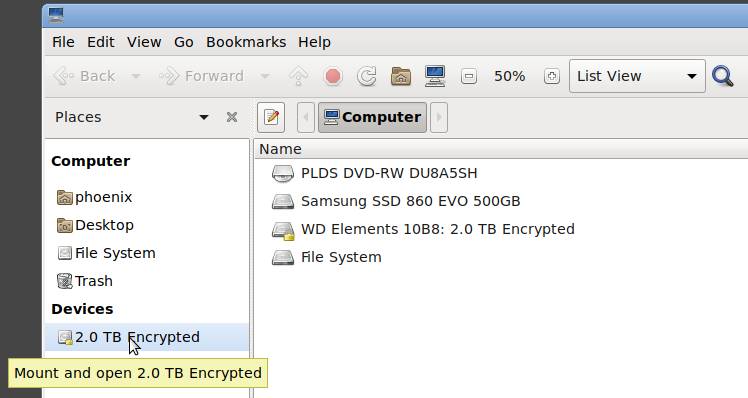
Congratulations, you just created your first fully encrypted external HDD!
The headline picture was created btw. by using the amazing dekryptize tool - a really cool ncurses animation to show how decrypting is definitely NOT working :-)
